Secure ASE Communication: Difference between revisions
No edit summary |
No edit summary |
||
| (5 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Introduction == | == Introduction == | ||
Using secure shell (SSH) between a configuration host and ASE and secure communication between TruView Central and ASE are intertwined. This procedure shows how to setup secure communication. Setting up SSH access is merely part of that process. | |||
| |||
== Solution == | == Solution == | ||
| Line 11: | Line 15: | ||
*Connect to the ASE | *Connect to the ASE | ||
Telnet (tcp/23) | Telnet (tcp/23). | ||
Depending on the ASE model, serial port settings are (8N1,9600) or (8N1,19200). | |||
*Login to ASE | *Login to ASE | ||
Default credentials admin/visual | Default credentials admin/visual. | ||
*Enter the security dialog and enter the settings as follows | *Enter the security dialog and enter the settings as follows | ||
You can add Host Address Security at a later stage. Be prepared to set a <passcode>. For security reasons, this should be different from the login password. | You can add Host Address Security at a later stage. Be prepared to set a <passcode>. For security reasons, this should be different from the login password. | ||
| Line 63: | Line 69: | ||
</pre> | </pre> | ||
*Locate and run IPTool located on TruView Central | *Locate and run IPTool located on TruView Central | ||
IPTool is an unsupported utility for use by Fluke Networks technical support. | IPTool is an unsupported utility for use by Fluke Networks technical support. | ||
<pre>C:\Program Files (x86)\Fluke Networks\Visual Performance Manager Server\iptool.exe</pre> | <pre>C:\Program Files (x86)\Fluke Networks\Visual Performance Manager Server\iptool.exe</pre> | ||
*From IPTool fetch any command for appflows or voip data by entering the passcode you have chosen in the previous step | *From IPTool fetch any command for appflows or voip data by entering the passcode you have chosen in the previous step | ||
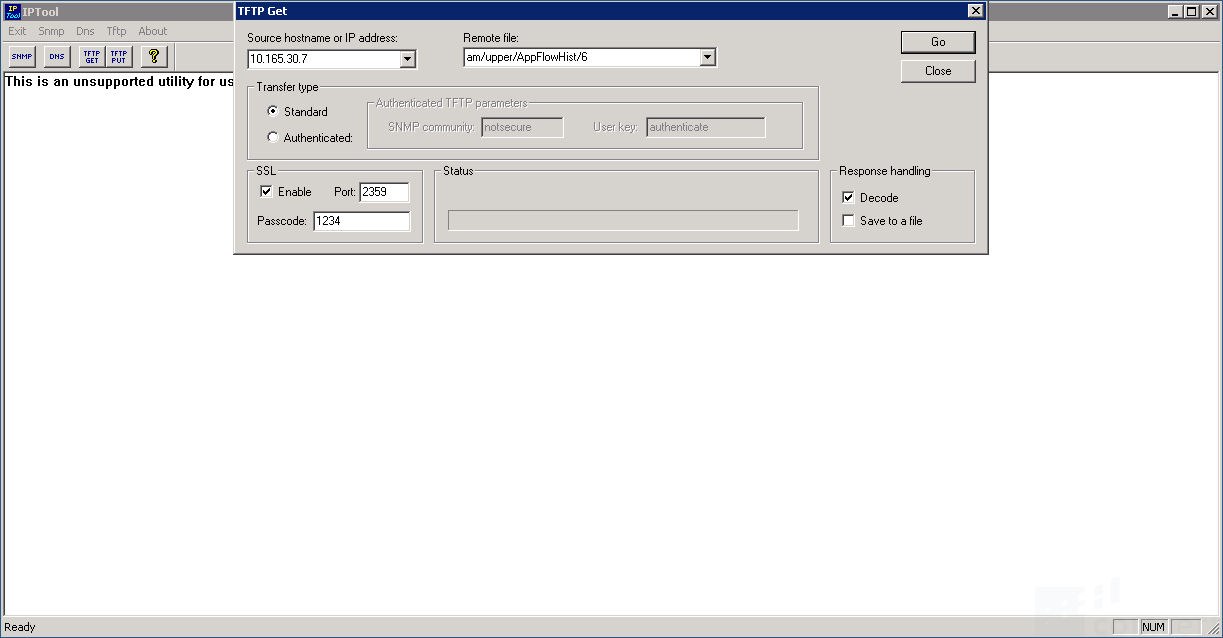
*Click '''TFTP GET''' in the top left corner of the windows and enter the ASE's settings per this example | *Click '''TFTP GET''' in the top left corner of the windows and enter the ASE's settings per this example | ||
[[File:IPToolTFTPGet.png|RTENOTITLE]] | [[File:IPToolTFTPGet.png|RTENOTITLE]] | ||
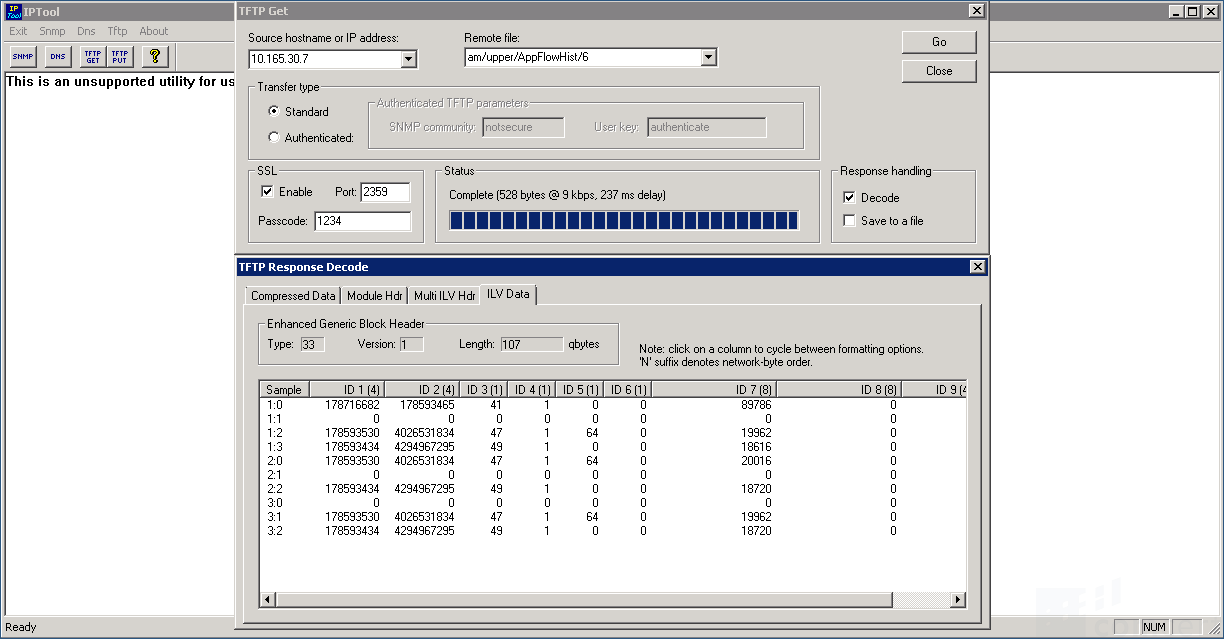
*Click '''Go'''. The results you get are irellevant at this time. The procedure enables secure communication on the ASE | *Click '''Go'''. The results you get are irellevant at this time. The procedure enables secure communication on the ASE | ||
[[File:TFTPResponseDecode.png|RTENOTITLE]] | [[File:TFTPResponseDecode.png|RTENOTITLE]] | ||
*Run the security dialog again and notice the value of Management passcode has changed to <span style="background-color:#FFFF00;">Set</span>. This confirms the TruView Central can communicate securely with the ASE and SSH access is granted | |||
<pre>CRT-DEV-ASE007> sh sec | |||
Security Level: Partial | |||
SSL TCP Port: 2359 | |||
Management passcode: Set | |||
Pending passcode: Ready | |||
Remote Console Protocol: SSH | |||
Host Address Security: Disabled | |||
Host Address Security Table: EMPTY</pre> | |||
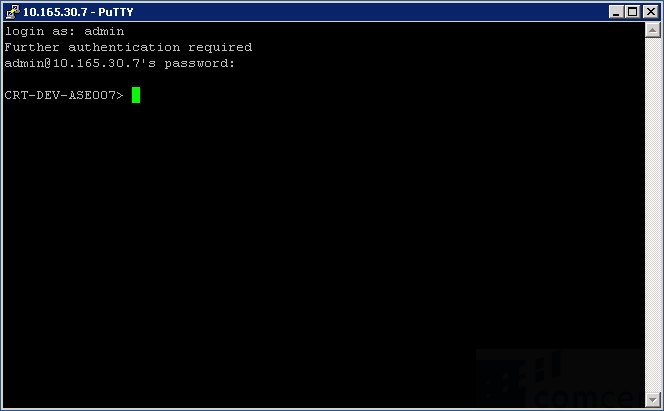
At this stage, you may login to the ASE using SSH (tcp/22). Putty is located on TruView Central. <span style="background-color:#FFFF00;">Only Putty on TruView Central can be used to connect securely to the ASE.</span> In future releases this restriction will be lifted. | At this stage, you may login to the ASE using SSH (tcp/22). Putty is located on TruView Central. <span style="background-color:#FFFF00;">Only Putty on TruView Central can be used to connect securely to the ASE.</span> In future releases this restriction will be lifted. | ||
| Line 82: | Line 99: | ||
[[File:TVCPutty.png|RTENOTITLE]] | [[File:TVCPutty.png|RTENOTITLE]] | ||
You can enhance security even further by enabling Host Address Security. Add a Host Address Security Table via the security dialog mentionned before. Only hosts with an IP address that belongs to a network in the table will be able to access the ASE using SSH. This has no effect on the ASE-to-TVC communication. | |||
Latest revision as of 07:05, 4 September 2017
Introduction
Using secure shell (SSH) between a configuration host and ASE and secure communication between TruView Central and ASE are intertwined. This procedure shows how to setup secure communication. Setting up SSH access is merely part of that process.
Solution
| Before secure communication can be configured, unsecure IP communication (Telnet) must be established between the ASE and TruView Central. If this is not allowed by your company's security policy, these steps must be completed in the lab. |
Enabling secure communication between the ASE, PAC and TruView Central should be the same for all ASEs running firmware version 6.9 or higher. This procedure has been tested on ASE Series 1900 and Series 400.
- Connect to the ASE
Telnet (tcp/23).
Depending on the ASE model, serial port settings are (8N1,9600) or (8N1,19200).
- Login to ASE
Default credentials admin/visual.
- Enter the security dialog and enter the settings as follows
You can add Host Address Security at a later stage. Be prepared to set a <passcode>. For security reasons, this should be different from the login password.
CRT-DEV-ASE007> sec
| Parameter | Value | Remarks |
| Security Level | Partial | - |
| SSL TCP Port | 2359 | This is the port for secure communication between ASE and TruView Central with the exception of Putty. You may choose any port except tcp/22. |
| Change Management Passcode | Y | - |
| Enter Management Passcode | <passcode> | - |
| Change Host Address Security Table | None | Can be added later |
Check the setttings and notice that the field Managent Passcode reads None. This is expected.
CRT-DEV-ASE007> sh sec
Security Level: Partial
SSL TCP Port: 2359
Management passcode: None
Pending passcode: Ready
Remote Console Protocol: SSH
Host Address Security: Disabled
Host Address Security Table: EMPTY
- Locate and run IPTool located on TruView Central
IPTool is an unsupported utility for use by Fluke Networks technical support.
C:\Program Files (x86)\Fluke Networks\Visual Performance Manager Server\iptool.exe
- From IPTool fetch any command for appflows or voip data by entering the passcode you have chosen in the previous step
- Click TFTP GET in the top left corner of the windows and enter the ASE's settings per this example
- Click Go. The results you get are irellevant at this time. The procedure enables secure communication on the ASE
- Run the security dialog again and notice the value of Management passcode has changed to Set. This confirms the TruView Central can communicate securely with the ASE and SSH access is granted
CRT-DEV-ASE007> sh sec
Security Level: Partial
SSL TCP Port: 2359
Management passcode: Set
Pending passcode: Ready
Remote Console Protocol: SSH
Host Address Security: Disabled
Host Address Security Table: EMPTY
At this stage, you may login to the ASE using SSH (tcp/22). Putty is located on TruView Central. Only Putty on TruView Central can be used to connect securely to the ASE. In future releases this restriction will be lifted.
You can enhance security even further by enabling Host Address Security. Add a Host Address Security Table via the security dialog mentionned before. Only hosts with an IP address that belongs to a network in the table will be able to access the ASE using SSH. This has no effect on the ASE-to-TVC communication.